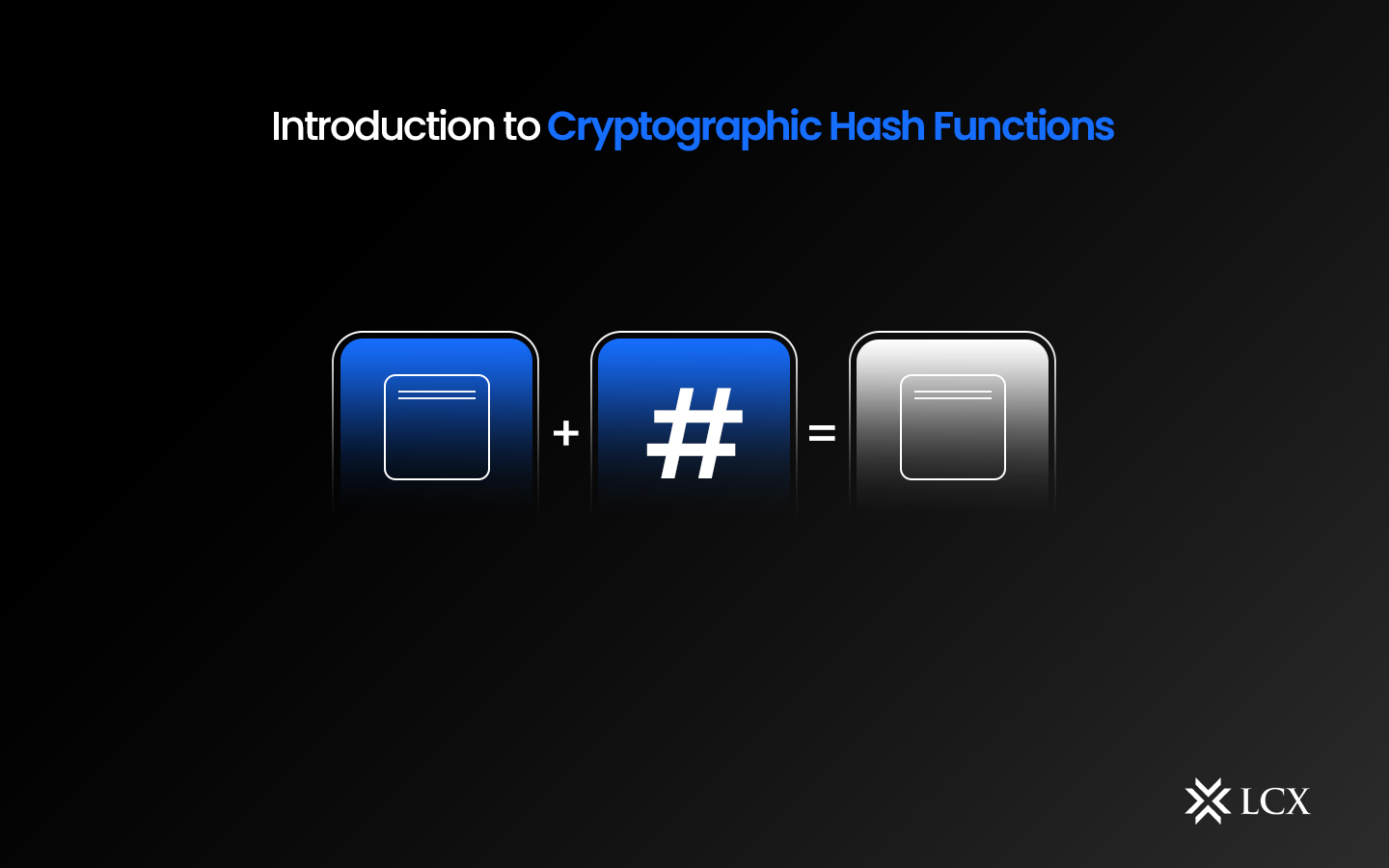
A cryptographic hash function is a mathematical algorithm that processes complex computations on an input of any size and returns a hash value, which is a fixed-length alphanumeric output. This process exhibits various essential characteristics:
- Input can be of any size or format.
- Always, the output is of a fixed length.
- It is exceedingly challenging to reverse the process and ascertain the input.
- Hashing is completely altered by even minute modifications to the input.
- Relationships and patterns among inputs are obscured.
These characteristics render cryptographic hashing indispensable for blockchain organization, security, and verification. Hashes effectively obfuscate sensitive data and facilitate the detection of tampering by means of deterministic yet unpredictable outputs.
Common Hash Functions — SHA-256 and More
There are numerous standard cypher functions that cover a wide range of use cases, including file verification and password protection. Several frequently cited examples include:
- SHA-256–256-bit algorithms are utilised extensively in blockchain and Bitcoin applications.
- MD5–128-bit sequences are frequently employed to verify file integrity.
- BLAKE2 is a flexible algorithm that incorporates keyed modes and hash trees.
- Scrypt is a memory-hard function that protects passwords from brute-force attacks.
- Bcrypt is an adaptive password cipher that employs salted keys to thwart rainbow table attacks.
The NSA devised SHA-256 function, which provides an exceptionally low collision rate. Every successive iteration of SHA exacerbates the weaknesses of preceding algorithms such as SHA-1 and MD5.
Hash Properties — Determinism, Efficiency and One-Way Nature
Cryptographic hash functions exhibit a number of desirable characteristics:
- Deterministic—Returns the exact same value for a specified input, irrespective of the environment or invocation.
- Efficient—Capable of rapidly hashing massive volumes of data with minimal processing overhead.
- One-way function—The hashing procedure cannot be reversed in order to recover the original input.
Hashes are ideally suited to facilitate distributed consensus in blockchain systems.
Hashing in Blockchain — Enabling Decentralized Consensus
Hash functions serve as the fundamental cryptographic elements that support proof-of-work and other blockchain consensus algorithms. More precisely, they enable the efficient verification of the integrity of distributed ledgers and data structures in the absence of centralized authorities.
Blockchains consist of blocks arranged in a sequential fashion, each comprising activity records that are built upon the preceding block. A distinct hash value is generated for each block by executing its entirety through a one-way hashing algorithm such as SHA-256.
By linking blocks in this manner, a chain is formed, given that the hash of the previous block is appended to each subsequent block. The integrity of this hash chain is maintained throughout all historical blocks, dating back to the initial Genesis block.
The hash value would instantly change if block data was tampered with, thereby compromising the validity of the chain and indicating corruption. This enables decentralized networks to verify the consistency of blockchains without relying on implicit trust but rather through hash comparisons.
Hash Functions for Efficient Data Indexing and Retrieval
In addition to facilitating optimized data retrieval, hashes generate unique identifiers in the form of fixed-length derivatives of inputs.
As an illustration, SHA-256 hashes of consistent size can function as pointers and references to access files or blockchain data without requiring the complete contents. This reduces bloated storage.
Compared to full replication, the use of hashes significantly reduces the amount of latency required to validate the state of a ledger across a distributed blockchain ecosystem. Nodes have the capability to exchange and authenticate 32-byte hashes as opposed to complete gigabyte-sized blocks. Rapid verification and scalability are facilitated by this.
Hash Trees (Merkle Trees) — Compressing Blockchain Data
Additionally, the mechanisms for more sophisticated blockchain data structures, such as hash trees, also known as Merkle trees, are derived from the distinctive characteristics of hashes.
By employing clever branching and utilizing hashes of hashes (referred to as parent and child), hash trees enable the verification of vast datasets with minimal storage. Interior parent hashes may be used to depict branches whose validity is verified by the children, as opposed to storing entire blocks.
By transmitting only the tiny top hashes, this facilitates the verification of massive datasets across peer networks in a streamlined fashion. The integrity of the hash tree structure is maintained due to the fact that altering any offspring would render the parents invalid.
Bitcoin utilizes Merkle trees as a means to store blockchain transaction data in an efficient manner, while also ensuring that it remains verifiable via cryptographic hashing. Merkle trees became prevalent in blockchain technology subsequent to the introduction of Bitcoin.
Hash-Based Signatures and Keys — Wallets, Addresses and Authorization
Furthermore, cryptographic hashes facilitate crucial authorization and security features of blockchain wallets and transactions via digital signatures, in addition to facilitating consensus and data structures:
- Blockchain transactions are signed with secret private keys to authorize activity.
- Hashing can be used to represent private keys for keyless security.
- By hashing the message and subsequently encrypting this hash using the private key, signatures are generated.
- Addresses and public keys are generated via hashes of public keys.
By employing one-way hash functions, these applications enable the authorization and ownership of wallet addresses and signatures to be verified while remaining anonymous. For blockchain scale, this is preferable to symmetric key encryption.
Hashing in Mining — Proof-of-Work Consensus
In conclusion, proof-of-work mining, the mechanism that drives consensus in protocols such as Bitcoin and Ethereum, relies heavily on hash functions.
The mining procedure entails the rapid generation of candidate block hashes through the estimation of trillions of nonce values and additional parameters. Due to the arbitrary nature of hashing output, incentives are distributed equitably in proportion to the amount of computing power expended.
To be valid, the block’s hash must commence with a specific quantity of 0 bits. This target of difficulty dictates the mining competition. One-way hashing precludes the computation of solutions in advance.
By employing hashes, miners demonstrate that solutions require random effort to discover. Hashing permits decentralized mining that is not centralized on administrators but rather operates on the basis of cryptographic confirmations.
Conclusion
In essence, cryptographic hash functions, such as SHA-256 and Merkle trees, are critical components that support decentralization, mining, security, and blockchain consensus.
Distributed verification of blockchain states and append-only ledger models that are resistant to revision is made possible by one-way hashing. These innovations, which originated in Bitcoin, form the basis of all cryptocurrencies founded on the blockchain.
Hash functions provide the dependable deterministic fingerprinting required to verify events and facts on public ledgers in the absence of centralized trust, despite protocol-specific variations. Predict that as blockchain technology advances, cryptographic hashes will continue to play a crucial role in enabling decentralization via mathematical means as opposed to human intervention.