In the realm of cryptography, the Secure Hash Algorithm 256 (SHA-256) stands as a pillar of security and trust. It’s a cryptographic hash function that underpins the security of various blockchain networks, most notably cryptocurrencies.
Encryption and hashing have been the central tenets of additional security modules as a result of the numerous advancements in network security. SHA 256 is one of the most popular hash algorithms. Despite the existence of other variants, SHA 256 has dominated real-world applications.
What Is Hashing?
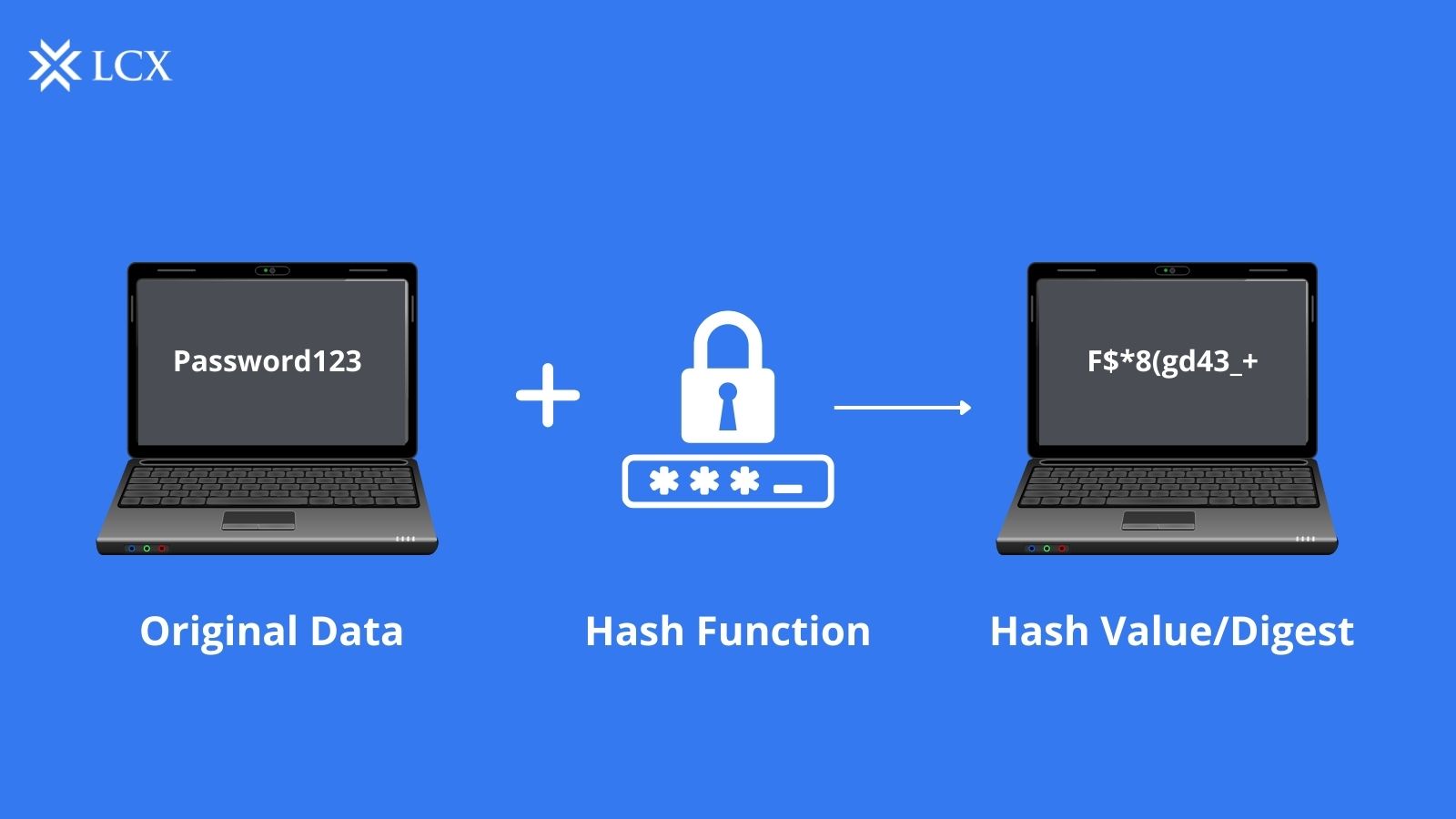
The process of hashing is the transformation of any information into another value. It comprises blocks of data that are transformed from the original string into a short, fixed-length key or value. It entails passing the data through a mathematical function that transforms it into a unique and intricate string of characters.
Hashing is a secure and efficient method for validating data integrity. When you hash a piece of data, you can compare the result to a known or expected value to verify that the data has not been altered or corrupted. If the hash values are identical, you can be confident that the data has not been altered since it was hashed.
An advantage of hashing is that it is irreversible. The hash value cannot be used to retrieve the original data. This property makes hashing beneficial for password storage, as it enables the storage of a password’s hash rather than the password itself. When a user inputs their password, the system can hash it and compare it to the previously stored hash value to determine if it is correct without requiring the actual password.
There are two principal uses for hashing:
Password Hashes:
Before being stored on a server, the majority of website servers convert user credentials into a hash value. It validates the authentication by comparing the newly calculated hash value to the one stored in the database.
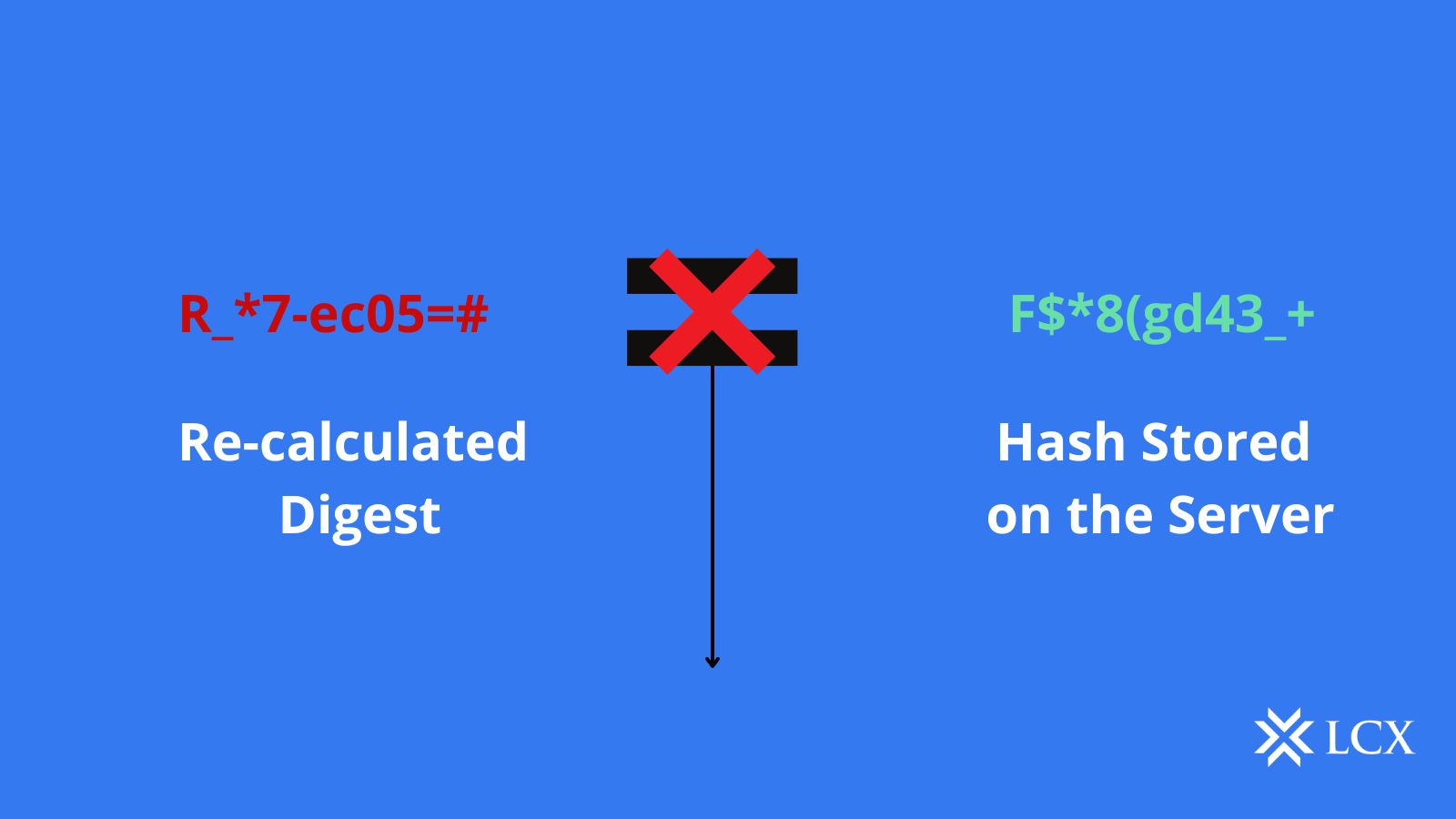
Integrity Verification:
When the user uploads a file to a website, the hash of the file is also shared. When a user downloads it, the hash can be recalculated and compared to ensure data integrity.

What Is the SHA-256 Algorithm?
SHA-256 (Secure Hash Algorithm 256) is a popular cryptographic algorithm that generates a 256-bit (32-byte) fixed-length hash value. The purpose of the SHA-256 algorithm is to generate a unique digital fingerprint for a message or file.
In order to generate a SHA-256 hash, the input data must be processed by a complex mathematical function that generates a unique output value. This output value is the hash of the input data.
Numerous applications employ the SHA-256 algorithm, including digital signatures, password authentication, and blockchain technology. Due to the uniqueness of the SHA-256 hash value, it is practically impossible to reverse-engineer the input data.
What Are the Characteristics of the SHA-256 Algorithm?
Message Length:
The cleartext should be less than 264 bits in length. To maintain the digest as random as possible, the size must be within the comparison region.
Digest Length:
The length of the hash digest should be 256 bits for the SHA-256 algorithm, 512 bits for SHA-512, etc. Typically, larger digests necessitate substantially more calculations at the expense of both time and space.
Irreversible:
By design, all hash functions, including the SHA-256, are irreversible. You should not obtain the plaintext if you already possess the digest, nor should the digest return its original value when it is passed through the hash function again.
Is SHA-256 Secure?
Despite the fact that no cryptographic algorithm is invulnerable to attack, the SHA-256 algorithm has withstood extensive analysis and the measure of time to remain an indispensable component of digital data security.
Combining intricate mathematical and bitwise operations, SHA-256 security generates the hash value.
It is extremely difficult to discover two inputs that produce the same hash with this design. However, SHA-256’s security is contingent on the correct implementation and robustness of the security protocols utilised by the application that employs it.
The prospect of a collision attack is a weakness of the SHA-256 algorithm. It takes place when two distinct inputs generate the same hash value. Theoretically, this is still possible with SHA-256, which generates 256-bit hash values (i.e., multiple possible outputs), despite the fact that it is extremely unlikely. A successful collision attack could compromise an application that uses SHA-256 hash values to verify data integrity.
What Are the Steps in SHA-256 Algorithm?
SHA-256 processes the input data through a series of mathematical operations known as rounds. Each round includes data preprocessing, message expansion, and a message compression function.
Here are the primary components of the SHA-256 algorithm:
- Data Preprocessing: The input data is padded and extended to ensure that its length is a multiple of 512 bits by appending a one-bit followed by zeros and then the length of the original message in bits.
- Message Expansion: The 512-bit input block is divided into 16 32-bit words and then expanded into 64 32-bit words via a series of logical operations.
- Message Compression: The expanded 64-word message block is then compressed through a series of 64 cycles, each of which consists of multiple steps:
- Determine the round constant: A unique 32-bit constant value is generated for each round based on its position in the sequence.
- Determine the message scheduling: The 64-word message block and round constant are utilised to generate a 64-entry message schedule. The working variables, which are 8 32-bit words that contain intermediate values during the hashing process, are updated in accordance with the message schedule and a series of logical operations.
- Calculate the hash value: Following completion of all 64 rounds, the final values of the working variables are combined to generate the 256-bit hash value.
The output of the SHA-256 hash algorithm is a 256-bit hash value that functions as a digital identifier of the input data.
Applications of SHA Algorithm
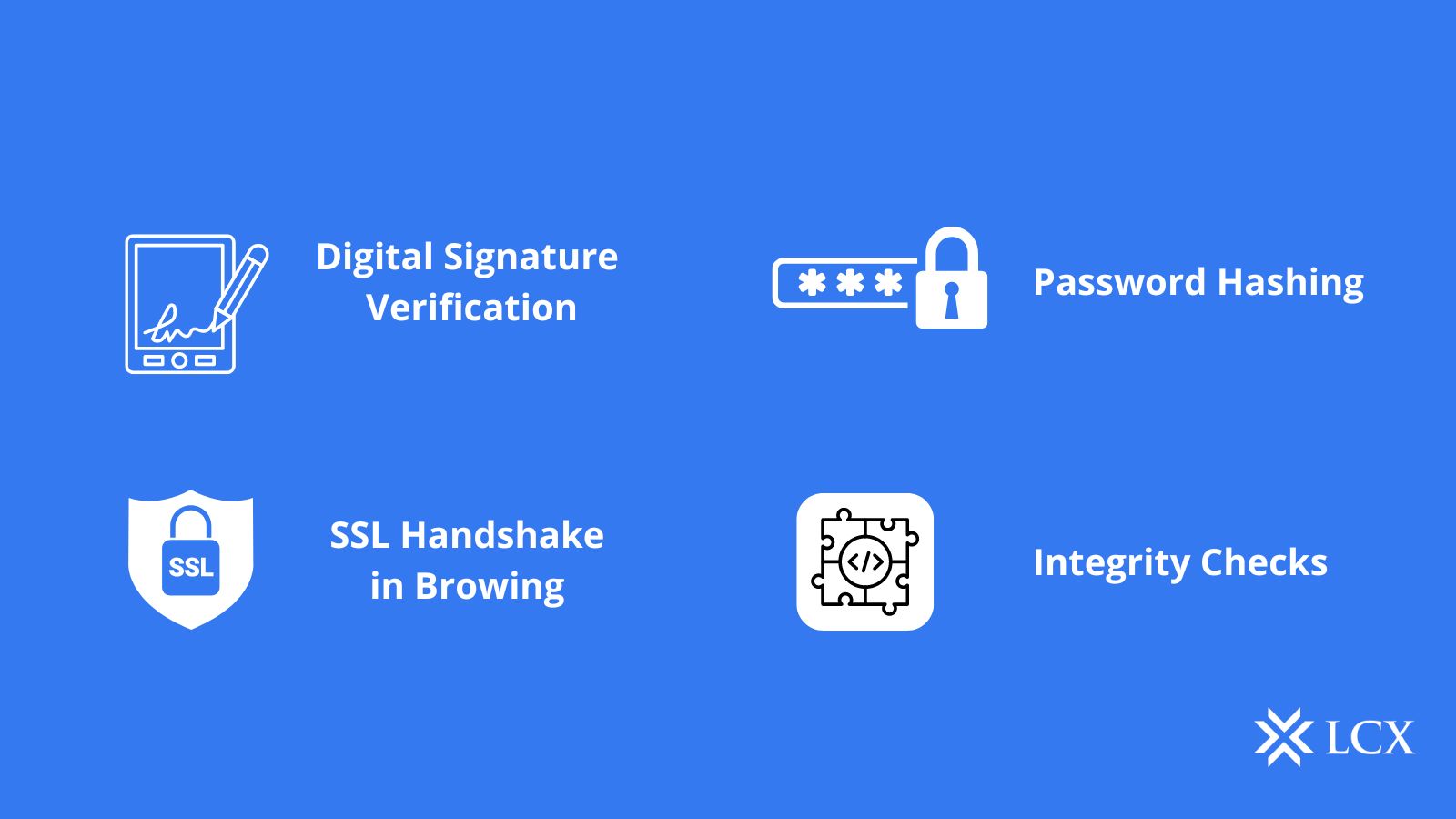
SHA algorithm is utilized in numerous locations, including those listed below.
Verification of Digital Signatures:
Digital signatures use asymmetric encryption to verify the authenticity of a document/file. Hash algorithms such as SHA 256 contribute significantly to the verification of the signature.
Password Hashing:
Websites store user credentials in a hashed format for two reasons. It promotes a sense of privacy and reduces the burden on the central database by ensuring that all digests are the same size.
SSL Handshake:
SHA functions are used to perform the SSL handshake, which is a crucial part of web browsing sessions. To establish a secure connection, your web browser and the web server must concur on encryption keys and hash authentication.
Integrity Checks:
As discussed previously, the SHA 256 algorithm and the MD5 algorithm are used to verify the integrity of files. It serves to preserve the full functionality of files and ensures that they were not modified in transit.
Conclusion
In the landscape of cryptography and cybersecurity, SHA-256 has cemented its status as a cornerstone of trust and security. Its role in securing cryptocurrencies like Bitcoin has propelled it into the spotlight, but its impact extends far beyond digital coins. From password protection to digital signatures, SHA-256’s complex and irreversible nature has proven its effectiveness in safeguarding sensitive information.
However, as technology evolves, the importance of staying vigilant and adapting to emerging cryptographic advancements remains crucial to ensure the continued integrity of our digital world.