Welcome to the third chapter of your crypto crash course! In Chapter 1, you explored the fundamentals of seed phrases and BIP39, the backbone of wallet recovery. In Chapter 2, we dived into crypto wallets, unravelling the role of public and private keys in securing transactions. Now, in Chapter 3, it’s time to decode the science behind cryptographic encryption—the battle between symmetric and asymmetric encryption.
The increasing rate of cybercrime has made cybersecurity a core function in recent years. It is more important than ever to protect and encrypt sensitive data. Encryption plays a major role in this process, transforming data into ciphertext using mathematical procedures known as encryption algorithms. Two types of encryption exist: symmetric key encryption and asymmetric key encryption.
Key Takeaways
- Symmetric key encryption: uses one shared key for faster encryption of large data, but it requires a secure way to share the key. Examples include AES, DES, and Blowfish.
- Asymmetric encryption: relies on two keys (public and private) for added security, solving the key distribution problem and powering secure communication like SSL/TLS and digital signatures.
- Speed vs. Security: Symmetric encryption is faster for large internal data, while asymmetric encryption is more secure for external communications.
- Hybrid Approach: HTTPS and other modern systems use asymmetric encryption to exchange a symmetric key for fast, secure data transmission.
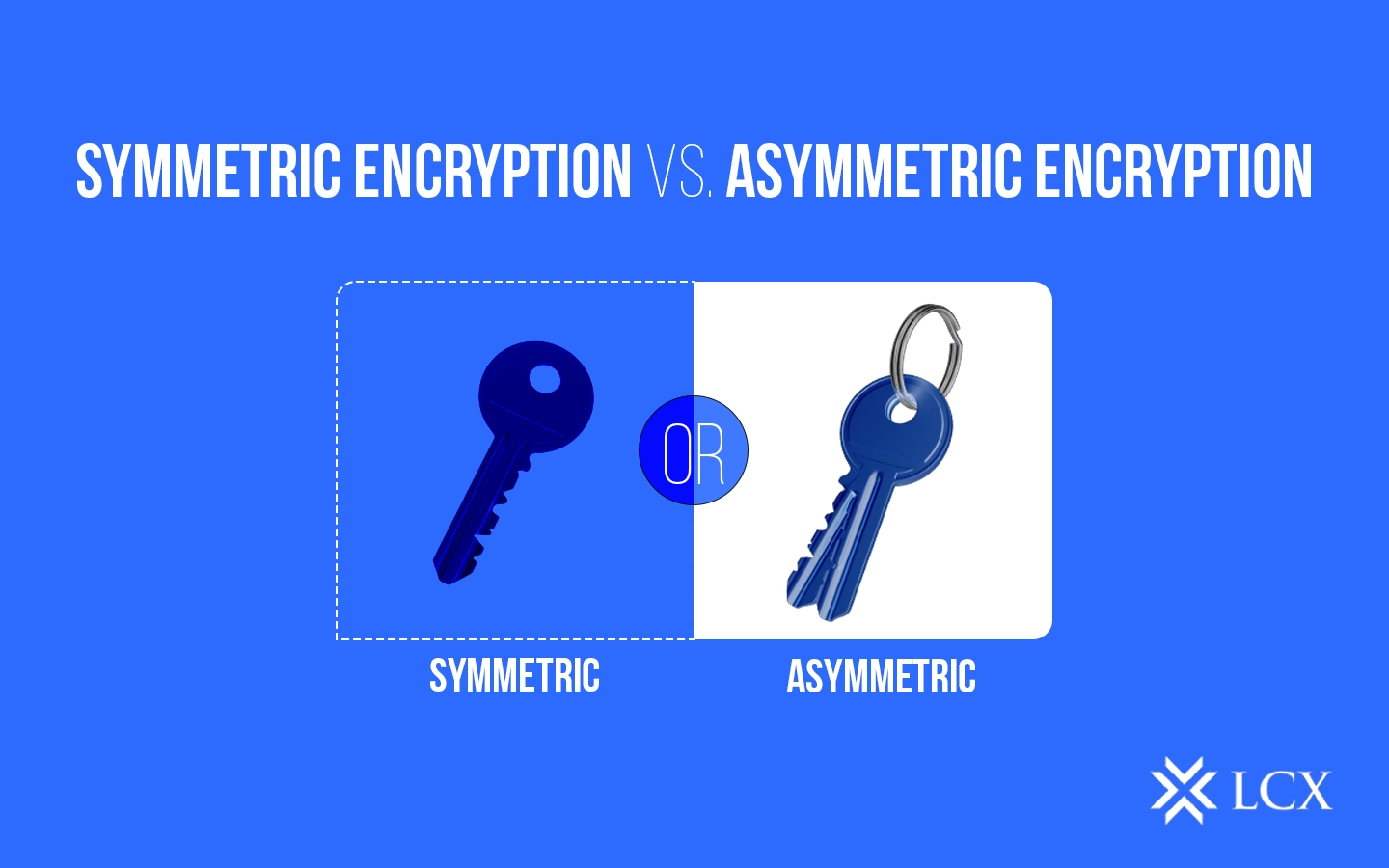
What is Symmetric Key Encryption?
Symmetric key encryption, or symmetric key cryptography, employs the same key to both encrypt and decrypt a message. This means that both the sender and receiver must have access to the same secret key to encode and decode the data.
Key Features of Symmetric Key Encryption
- One key is used for both encryption and decryption.
- More efficient and faster for large volumes of data.
- It requires a secure method to share the key between the sender and receiver.
- AES, DES, and Blowfish are common algorithms.
- Used in file encryption, VPNs, and secure data storage.
Benefits of Symmetric Encryption
Security: Data is strongly protected by symmetric encryption, utilizing a shared key for both encryption and decryption. This system helps prevent unauthorized access. Advanced Encryption Standard (AES), Data Encryption Standard (DES), and International Data Encryption Algorithm (IDEA) are commonly used algorithms.
Efficiency: Symmetric encryption is cost- and time-efficient as it requires less processing power and fewer resources.
Speed: It is faster than other encryption types since the same key is used for both processes, making it ideal for applications that require rapid encryption and decryption.
Compatibility: Symmetric encryption integrates easily into existing applications and systems, making it compatible with the majority of hardware and software platforms.
Simplicity: With only one key required for both encryption and decryption, symmetric encryption is straightforward to implement and widely used in applications requiring simple encryption mechanisms.
What is Asymmetric Key Encryption?
Asymmetric encryption, or asymmetric key cryptography, uses a pair of encryption keys to encrypt and decrypt data. It employs two distinct keys – a public key, and a private key – enhancing security during communication between sender and receiver.
Key Features of Asymmetric Key Encryption
- Uses two keys: a public key for encryption and a private key for decryption.
- More secure but slower compared to symmetric encryption.
- Reduces exposure risk by eliminating the need to share the private key.
- RSA, ECC, and Diffie-Hellman are common algorithms.
- Used in digital signatures, SSL, TLS, and secure email communication.
Benefits of Asymmetric Encryption
Security: Provides strong data protection as the private key is kept confidential, making unauthorized access significantly more difficult.
Authentication: Verifies the sender’s identity and helps prevent fraud and malicious attacks, as only the corresponding private key can decrypt messages encrypted with the public key.
Key Distribution: Does not require a secure channel for key distribution since users have unique public-private key pairs. Only the private key can decrypt messages encrypted with the public key, simplifying key management.
Flexibility: Widely applicable for secure email communication, online banking, and secure access to network systems, provided the private key remains secure.
Non-Repudiation: The public-private key pairing ensures non-repudiation, meaning the sender cannot deny sending a message, as only the sender’s private key could have encrypted it.
Differences Between Symmetric and Asymmetric Encryption
| Criteria | Symmetric Key Encryption | Asymmetric Key Encryption |
| Number of Keys | Single key shared between sender and receiver. | Two keys: Public key (shared) and Private key (kept secret). |
| Encryption/Decryption Process | Same key is applied for both encrypting and decrypting data. | Public key encrypts the data, while the private key decrypts it (or vice versa depending on the operation). |
| Speed & Performance | Faster due to simpler algorithms and less computational load. | Slower due to complex mathematical operations and longer key lengths. |
| Security | Secure only if the key is shared safely; vulnerable if the key is intercepted. | Higher security as the private key is never shared; resistant to man-in-the-middle attacks. |
| Key Distribution Challenge | Requires a secure channel for key distribution. | Solves the key distribution problem; the public key can be openly shared. |
| Confidentiality & Integrity | Ensures confidentiality but doesn’t inherently provide authentication. | Provides confidentiality, authentication, and non-repudiation. |
| Computational Overhead | Low – ideal for encrypting large volumes of data quickly. | High – resource-intensive due to asymmetric cryptography operations. |
| Key Size | Shorter keys (e.g., 128-bit, 192-bit, 256-bit in AES). | Much longer keys (e.g., 2048-bit or 4096-bit in RSA). |
| Algorithm Examples | AES, DES, 3DES, RC4, Blowfish, Twofish. | RSA, ECC, DSA, ElGamal. |
| Use Cases | Data encryption at rest (files, databases), securing internal systems (VPNs), disk encryption (e.g., BitLocker). | Secure key exchange, digital signatures, SSL/TLS (HTTPS), and blockchain (e.g., wallets). |
| Scalability | Less scalable – key management becomes complex with more users. | More scalable – no need for shared keys with every communication partner. |
| Hybrid Use | Typically used for bulk data encryption after secure key exchange. | Often combined with symmetric encryption to establish session keys (e.g., SSL/TLS handshake). |
| Vulnerabilities | Susceptible if key is exposed during distribution or storage. | Susceptible to brute-force or quantum attacks if key lengths are inadequate. |
| Best Suited For | High-speed encryption of large datasets within trusted networks. | Secure communication over untrusted networks and authentication of users/systems. |
How is Each Type of Encryption Used?
Symmetric encryption is widely adopted to secure emails, file transfers, and VPNs. The Advanced Encryption Standard (AES) is the leading symmetric algorithm, with AES-256 being the strongest variant, trusted by the U.S. government for protecting classified data. DES, once the standard, was replaced due to its short key length, making it vulnerable to brute-force attacks. Stronger alternatives like AES and Triple DES (3DES) are now preferred.
While less common, asymmetric encryption is increasingly used in high-security environments such as online banking and cryptocurrency. RSA remains the most widely used asymmetric algorithm, with RSA-2048 providing robust protection, also endorsed by the U.S. government.
In conclusion, both symmetric and asymmetric encryption offer distinct advantages depending on the application. Understanding their differences enables organizations to choose the most suitable method to protect sensitive information.
FAQs
What is the advantage of Symmetric Encryption over Asymmetric Encryption?
Symmetric encryption is swifter and more efficient, making it ideal for encrypting large volumes of data. Asymmetric encryption, on the other hand, excels in secure key exchange and digital signatures.
What are common applications for Asymmetric Encryption Algorithms?
Asymmetric encryption is used to ensure secure Internet communication, including email, e-commerce, and online banking. It is also widely employed in digital signatures and secure key exchange protocols.
Symmetric or Asymmetric: Which encryption is more secure?
Both methods are secure when properly implemented and managed. Symmetric encryption is preferred for encrypting large datasets, while asymmetric encryption is considered more secure for secure communication over untrusted networks.
What are the basic types of encryption systems and how do they differ?
The two main types are symmetric encryption and public-key (asymmetric) encryption. Symmetric encryption uses a single shared key, while asymmetric encryption uses two keys – one for encryption and one for decryption. Symmetric is faster and more efficient, while asymmetric offers enhanced security for specific use cases.
Did You Know?
“The concept of asymmetric cryptography, or public-key cryptography, was so groundbreaking that when it was first discovered by British intelligence in the early 1970s, it was classified as a military secret and kept hidden from the public for years.”